Mandiant’s X account encountered a breach in security, which was tactically exploited by cybercriminals to enable the theft of cryptocurrency by spreading deceptive links.
Mandiant, the cybersecurity firm associated with Google, experienced a cyber attack on its X (formerly Twitter) account. The breach, believed to be a result of a brute-force password attack during team transitions and changes in the 2FA policy, allowed threat actors to temporarily take control.
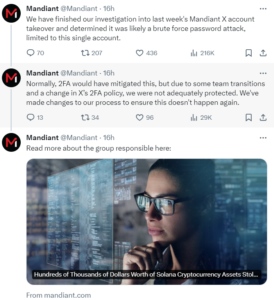
By exploiting Mandiant’s compromised X account, the attackers directed more than 123,000 followers to a phishing page specifically designed for stealing cryptocurrency. Through swift action and collaboration with X, Mandiant was able to promptly regain control. Subsequent investigations revealed the use of a well-known wallet drainer called CLINKSINK, which had been employed since December as part of a larger campaign targeting users of the Solana (SOL) cryptocurrency.
This elaborate scheme involved at least 35 affiliate IDs connected to a shared Drainer-as-a-Service (DaaS), which facilitated cryptocurrency theft with the operators receiving a 20% share. By taking over hijacked X and Discord accounts, the threat actors distributed phishing pages related to cryptocurrencies, disguising themselves as reputable platforms like Phantom and DappRadar.
Unsuspecting visitors who fell victim to these deceptive pages unknowingly linked their crypto wallets, granting authorization for the perpetrators to drain funds through transactions to the drainer service. The estimated amount stolen from these orchestrated attacks is a staggering minimum of $900,000.
This breach is part of a larger wave of X account compromises in 2024, affecting verified entities. Notably, even the U.S. Securities and Exchange Commission (SEC) fell victim to a similar breach, resulting in a misleading announcement regarding Bitcoin ETF approvals and subsequent market instability.
The increasing frequency of such attacks highlights the ongoing threat faced by X users. Verified government and business accounts are increasingly targeted to lend credibility to cryptocurrency scams, phishing attempts, and drainer promotions. As a result, users are bombarded with malicious cryptocurrency advertisements, fraudulent airdrops, and various scams, raising serious concerns about the security resilience of X.
The occurrence reflects a recurring pattern of X account breaches, underscoring the urgent requirement for strong security protocols, such as 2FA, to counter the constantly evolving cyber risks in the cryptocurrency domain. In light of the ongoing transformation of the digital landscape, individuals and institutions alike must remain exceptionally vigilant in order to protect their digital assets from the relentless pursuit of unauthorized entry by malicious entities.
sharanukalyan
Related posts
1 Comment
Leave a Reply Cancel reply
Categories
- Blog (9)
- Chrome (2)
- cisco (1)
- Cloud security (1)
- Crypto Scam (1)
- Cryptocurrency (2)
- Cryptojacking (1)
- CVE (20)
- Cyber News (9)
- cyber security (2)
- Data breaches (1)
- Email security (1)
- Email spoofing (1)
- Fashion (1)
- Guide (1)
- malware (1)
- Malware attack (1)
- Mandiant (1)
- News (15)
- OpenSSH (1)
- Password attack (1)
- Patch (6)
- Payment Security (1)
- phishing (1)
- ransomware (2)
- RCE (9)
- SMTP Smuggling (1)
- SQL injection attack (1)
- XSS attacks (2)
- zeroday (9)


Neat gear! How can I get buy it?